| |
Home / Accueil

Call For Papers
Research
Sponsors
History
|
| |
|
|
| |
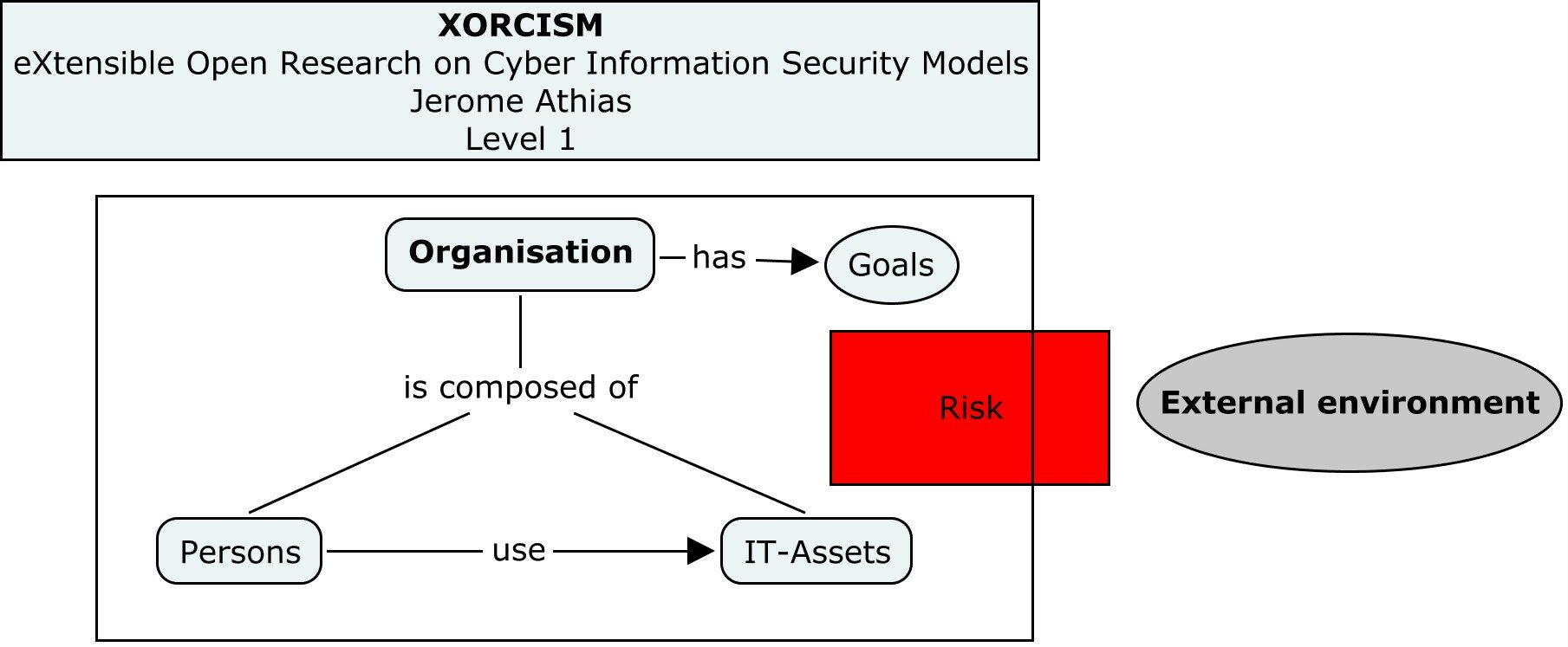
XORCISM
eXpandable Open Representation of Cyber Information Security Management
An eXpandable Open Research on Cyber Information Security Models
The XORCISM Model is built around various Open Information Security Data Models, Specifications, Standards, Frameworks, Guidelines, Architectures, Best Practices, Protocols and Vocabularies (Taxonomies/Ontologies).
Current version: DRAFT 1.0.0 beta
Documentation
XORCISM Overview and Concepts
Author: Copyright (C) 2013-2014
Last Update:
All trademarks and registered trademarks are the property of their respective owners.
Download the XORCISM Poster (version 0.7)
Access the XORCISM github repository for tools and documentation.
Objectives
Better IT Security Governance by facilitating Cyber Risk Management with real-time Security Metrics.
Improved Security Posture visibility and the adoption of cybersecurity practices for reducing cyber risks.
Risk-01: Link between Management and Technical levels
Interoperability, Information sharing, Automation
Inter-exchange needs Standards, or at least Specifications, and structured Common Vocabularies (Taxonomies/Ontologies).
XORCISM facilitates the Implementation and use of Open Specifications, Standards and Repositories. (Object-oriented programming (OOP)) for tactical and strategic cyber security.
Currently supported or integrated Data Models and Specifications
Asset Identification (AI)

Asset Reporting Format (ARF)
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Configuration Enumeration (CCE)
Common Vulnerabilities and Exposures (CVE)
Common Vulnerability Scoring System (CVSS)
Common Weakness Enumeration (CWE)
Cyber Observable eXpression (CybOX)
Default Passwords Enumeration (DPE)
Incident Object Description Exchange Format (IODEF)
Inventory of Standards Relevant to Cloud Computing
ISO Country Codes
Malware Attribute Enumeration and Characterization (MAEC)
Malware Metadata Exchange Format (MMDEF)
NIST SP 800-53 Security Control Families
North American Industry Classification System
Open Vulnerability and Assessment Language (OVAL)
Security Content Automation Protocol (SCAP)
Structured Threat Information eXpression (STIX)

Image taken from cyber.st.dhs.gov
Vocabulary for Event Recording and Incident Sharing (VERIS)
Extensible Configuration Checklist Description Format (XCCDF)
And some others/new ones (i.e.: A Vulnerability Data Model).
See also: IETF Vulnerability Data Model
Extensions, partially supported specifications, references
Abu Dhabi Information Security Programme
Architectural Model
Asset Summary Reporting (ASR)
Build Security In (BSI)
CERT Resilience Management Model (CERT-RMM)
Cloud Controls Matrix (Cloud Security Alliance - CSA)
Cybersecurity Information Exchange Techniques (CYBEX) Software Defined Perimeter Working Group (SDP)
Amazon Web Services – AWS Security Best Practices
Common Event Expression (CEE)
Continuous Asset Evaluation, Situational Awareness, and Risk Scoring (CAESARS)
iPost Scoring Methodology
Common Configuration Scoring. System (CCSS)
Center for Internet Security (CIS) Benchmarks
Common Remediation Enumeration (CRE)
DoD Information Assurance Risk Management Framework (DIARMF)
Intermediary Vulnerability Information Language (IVIL)
IODEF for Structured Cyber security Information (IODEF-SCI). MILE working group (Takahashi, 2013)
Distributed Audit Service (XDAS)
Common Vulnerability Reporting Framework (CVRF)
Weakness Risk Analysis Framework (CWRAF)
Weakness Scoring System (CWSS)
COSO
Cybersecurity Framework, Compendium
CIP-CSF Mind map
Factor Analysis of Information Risk (FAIR)
FrameworkX (TM Forum)
IFX Forum Framework
Information Risk Analysis Methodology (IRAM) of ISF (Information Security Forum)
GRC Repository
ICS Security Standard (Qatar)
Intrusion Detection Message Exchange Format (IDMEF)
IODEFbis
ISO 27000/ISO 27001 Information Security Risk Management System
ISO/IEC 19770
ISO 31000 Enterprise Management
Making Security Measurable (MSM)
NERC CIP (North American Electric Reliability Corporation, Critical Infrastructure Protection)
Network Defense Data Models (NDDM)
NIST 800-53
NIST 800-37
Open Automated Compliance Expert Markup Language (O-ACEML)
Open Checklist Interactive Language (OCIL)
Open Information Security Management Maturity Model (O-ISM3)
Open Web Application Security Project (OWASP)
OpenIOC (pyioc)
Open Threat Exchange (OTX)
The Collective Intelligence Framework (CIF)
Penetration Testing Execution Standard
Real-time Inter-network Defense (RID) RFC 6545 (Moriarty, 2012), RFC 6546 (Trammell, 2012)
Risk Taxonomy Technical Standard
SANS- Twenty Critical Security Controls for Effective Cyber Defense
Security Description and Exchange Format (SecDEF)
Security Battleground
Situational Awareness Reference Architecture (SARA)
Software Assurance (SwA) Competency Model
SWID tags ISO/IEC 19770
The Open Group Architecture Framework (TOGAF)
Traffic Light Protocol (TLP) Matrix
Trusted Automated eXchange of Indicator Information (TAXII)
Trust Model for Security Automation Data (TMSAD)
XEP-0268
SES - Security Event System
Web Application Security Consortium (WASC) (Threat Classification)
Known Weaknesses and Notes
The relationships between the entities can be easily extended. (i.e.: FINDING)
ENDPOINT is more granular than RFC 5209 (DEVICECOMPONENT), see also Connection_End_Point in NDDM
DEVICECOMPONENT (i.e.: SIM Card, Transistor, Processor) should be extended (DEVICECOMPONENTCATEGORY, MANUFACTURER... + WHITELIST, BLACKLIST)
XORCISM uses a CONFIDENCELEVEL attached to many information collected, missing in many Specifications.
Also the TRUSTLEVEL could be better defined as a TRUSTRELATIONSHIP
Lack in Operational (and Management) level
Implementation of RACI matrix
Use of ORGANISATION instead of ORGANIZATION, as per OASIS xNL used in Asset Identification 1.1 Note: It could be widely extended using other organization schemas.
Incomplete, non-exhaustive
Not fully compliant with the specifications. Database indexing: duplicated data attributes for easier programming and tests. (CPEID)
Would need more GUIDs (Synthetic IDs) (see DIDA)
Database Naming Convention for (relationships) tables:
ASSETFORORGANISATION (Organisation's Assets) vs VULNERABILITYPATCH (Patches for a Vulnerability) vs SCORINGSYSTEMFORMULAS (Scoring Formulas for a Scoring System)
CONTACT (CONTACTYPE) is NOT a PERSON, see Risk Taxonomy
"Contact is the probable frequency, within a given timeframe, that a threat agent will come into contact with an asset."
ADDRESS is NOT a PERSON's address nor an ORGANISATION's address, see CybOX AddressObjectType
The AddressObjectType is intended to characterize cyber addresses.
Examples (CategoryType): e-mail, mac, ipv4-addr
XORCISM includes ROPCHAIN, ROPGADGET ROP (Return-oriented programming) objects.
Software Vulnerability Exploitation Trends
OS Comes from first implementation: CPE+LOCALE
The RISKRATING depends of the Factors used into the METHODOLOGY
Use Cases
Anomaly detection and reaction
Application Security (APPSEC)
Automation
Big Data
Continuous Security Monitoring
Critical Infrastructure and Sensitive Information
Cyber Crime
Cyber Defense
Cyber Intelligence
Cyber Protection
Cyber Security
Forensics
Incident Response
Information Security (INFOSEC)
Internal and External Threat Mitigation
Interoperability
Malware Analysis
Network Security
Penetration Testing (PENTESTS)
Predictive Security Intelligence
Remediation
Resilience
Secure Configuration Management
Situational Awareness
Strategic Security
Vulnerability Assessment
Vulnerability Management
...
Currently Non-applicable Use Cases, Poor Implementation, Out of Scope
Chain of Trust
Cryptography
DRM
Identity Management
Keys Management (SSH, PGP, EFS, LUKS...)
See: OASIS Key Management Interoperability Protocol (KMIP) TC
Patch Management, Remediation
Project/Tasks Management
PRINCE2, COBIT, ITIL
...
List of Entities, Tables, Relationships (version 0.7)
ACCOUNT
ACRONYM
ACTION
ACTIONACTION
ACTIONACTIONARGUMENTNAME
ACTIONACTIONNAME
ACTIONACTIONTYPE
ACTIONALIAS
ACTIONARGUMENTNAME
ACTIONCONTEXT
ACTIONCYBEROBJECT
ACTIONDESCRIPTION
ACTIONDISCOVERYMETHOD
ACTIONNAME
ACTIONOBJECTASSOCIATIONTYPE
ACTIONPERTINENTCYBEROBJECTPROPERTY
ACTIONPOOL
ACTIONRELATIONSHIPTYPE
ACTIONSTATUS
ACTIONTAKEN
ACTIONTAKENFORINCIDENT
ACTIONTAKENFORTHREATCAMPAIGN
ACTIONTYPE
ACTIVATIONZONE
ACTIVATIONZONEFORATTACKPATTERN
ADDRESS
API
APIFUNCTION
APIMEMORYADDRESS
APIPLATFORM
APPLICATION
APPLICATIONFORASSET
APPLICATIONFUNCTION
APPLICATIONPERSON
ARCHITECTURALPARADIGM
ARCHITECTURALPARADIGMFORTECHNICALCONTEXT
ARFASSET
ARFASSETFORASSETS
ARFEXTENDEDINFO
ARFEXTENDEDINFOFORARFEXTENDEDINFOS
ARFEXTENDEDINFOS
ARFOBJECTREF
ARFOBJECTREFARFASSET
ARFOBJECTREFREPORT
ARFOBJECTREFREPORTREQUEST
ARFRELATIONSHIP
ARFRELATIONSHIPARFASSET
ARFRELATIONSHIPFORARFRELATIONSHIPS
ARFRELATIONSHIPREPORT
ARFRELATIONSHIPREPORTREQUEST
ARFRELATIONSHIPS
ARITHMETICFUNCTION
ARITHMETICOPERATION
ARTIFACT
ARTIFACTHASHVALUE
ARTIFACTPACKAGING
ARTIFACTTYPE
ASSET
ASSETADDRESS
ASSETBLACKLIST
ASSETCREDENTIAL
ASSETCRITICALITYLEVEL
ASSETCRITICALITYLEVELFORASSET
ASSETDEVICE
ASSETFORASSET
ASSETFORMISSION
ASSETFORORGANISATION
ASSETFORTHREATACTORTTP
ASSETFUNCTION
ASSETFUNCTIONFORASSET
ASSETLOCATION
ASSETLOCATIONFORASSET
ASSETMANAGEMENT
ASSETMANAGEMENTFORASSET
ASSETOPERATIONALATTRIBUTE
ASSETOWNERSHIP
ASSETPHYSICALLOCATION
ASSETRELATIONSHIP
ASSETREPORTCOLLECTION
ASSETRISKRATING
ASSETROLE
ASSETROLEFORASSET
ASSETS
ASSETSYNTHETICID
ASSETSYNTHETICIDFORASSET
ASSETVALUE
ASSETVALUEFORASSET
ASSETVARIETY
ASSETVARIETYFORASSET
ASSETWHITELIST
ATTACHMENT
ATTACKCONSEQUENCE
ATTACKCONSEQUENCEFORCAPEC
ATTACKCONSEQUENCESCOPE
ATTACKCONSEQUENCESCOPEFORATTACKCONSEQUENCE
ATTACKEXAMPLE
ATTACKEXAMPLEFORATTACKPATTERN
ATTACKMETHOD
ATTACKMETHODFORATTACKPATTERN
ATTACKPATTERN
ATTACKPATTERNFORTHREATACTORTTP
ATTACKPAYLOAD
ATTACKPAYLOADENCODER
ATTACKPAYLOADFORATTACKPATTERN
ATTACKPAYLOADIMPACT
ATTACKPAYLOADIMPACTFORATTACKPATTERN
ATTACKPREREQUISITE
ATTACKPREREQUISITEFORCAPEC
ATTACKPURPOSE
ATTACKPURPOSEFORATTACKPATTERN
ATTACKRESOURCE
ATTACKRESOURCEFORCAPEC
ATTACKSCENARIO
ATTACKSURFACE
ATTACKSURFACEFORATTACKPATTERN
ATTACKSURFACELOCALITY
ATTACKSURFACELOCALITYFORATTACKSURFACE
ATTACKSURFACESERVICE
ATTACKSURFACETYPE
ATTACKSURFACETYPEFORATTACKSURFACE
ATTACKTECHNICALIMPACT
ATTACKTECHNICALIMPACTFORATTACKCONSEQUENCE
ATTACKTOOL
ATTACKTOOLFORTHREATACTORTTP
ATTACKTOOLMODULE
ATTACKTOOLTYPE
ATTACKVECTOR
AUTHOR
BEGINFUNCTION
BENCHMARK
BENCHMARKCHECK
BENCHMARKCHECKCONTENTREF
BENCHMARKCHECKEXPORT
BENCHMARKCHECKFORBENCHMARKRULE
BENCHMARKCHECKFORBENCHMARKRULERESULT
BENCHMARKCHECKIMPORT
BENCHMARKCHECKLIST
BENCHMARKCOMPLEXCHECK
BENCHMARKCOMPLEXCHECKFORBENCHMARKRULE
BENCHMARKCOMPLEXCHECKFORBENCHMARKRULERESULT
BENCHMARKDCSTATUS
BENCHMARKDESCRIPTION
BENCHMARKFIXINSTANCE
BENCHMARKFIXTEXT
BENCHMARKFIXTEXTFIXACTION
BENCHMARKFRONT
BENCHMARKGROUP
BENCHMARKGROUPCONFLICT
BENCHMARKGROUPDCSTATUS
BENCHMARKGROUPDESCRIPTION
BENCHMARKGROUPFORBENCHMARK
BENCHMARKGROUPMETADATA
BENCHMARKGROUPQUESTION
BENCHMARKGROUPREFERENCE
BENCHMARKGROUPREQUIRE
BENCHMARKGROUPSTATUS
BENCHMARKGROUPTITLE
BENCHMARKGROUPWARNING
BENCHMARKMESSAGE
BENCHMARKMESSAGEFORBENCHMARKRULERESULT
BENCHMARKMETADATA
BENCHMARKMODEL
BENCHMARKNOTICE
BENCHMARKOVERRIDE
BENCHMARKOVERRIDEFORBENCHMARKRULERESULT
BENCHMARKPLAINTEXT
BENCHMARKPLATFORM
BENCHMARKPLATFORMFORBENCHMARK
BENCHMARKPLATFORMFORBENCHMARKGROUP
BENCHMARKPLATFORMFORBENCHMARKPROFILE
BENCHMARKPLATFORMFORBENCHMARKRULE
BENCHMARKPLATFORMFORBENCHMARKTESTRESULT
BENCHMARKPROFILE
BENCHMARKPROFILEDCSTATUS
BENCHMARKPROFILEDESCRIPTION
BENCHMARKPROFILEFORBENCHMARKTAILORING
BENCHMARKPROFILEMETADATA
BENCHMARKPROFILEREFERENCE
BENCHMARKPROFILEREFINERULE
BENCHMARKPROFILEREFINERULEREMARK
BENCHMARKPROFILEREFINEVALUE
BENCHMARKPROFILEREFINEVALUEREMARK
BENCHMARKPROFILESELECT
BENCHMARKPROFILESELECTREMARK
BENCHMARKPROFILESETCOMPLEXVALUE
BENCHMARKPROFILESETCOMPLEXVALUEREMARK
BENCHMARKPROFILESETVALUE
BENCHMARKPROFILESETVALUEREMARK
BENCHMARKPROFILESTATUS
BENCHMARKPROFILETITLE
BENCHMARKREAR
BENCHMARKREFERENCE
BENCHMARKREMARK
BENCHMARKRESULTINSTANCE
BENCHMARKRULE
BENCHMARKRULECONFLICT
BENCHMARKRULEDCSTATUS
BENCHMARKRULEDESCRIPTION
BENCHMARKRULEFIXACTION
BENCHMARKRULEFIXTEXT
BENCHMARKRULEFORBENCHMARK
BENCHMARKRULEFORBENCHMARKGROUP
BENCHMARKRULEIDENT
BENCHMARKRULEIDENTFORBENCHMARKRULE
BENCHMARKRULEIDENTFORBENCHMARKRULERESULT
BENCHMARKRULEMETADATA
BENCHMARKRULEPROFILENOTE
BENCHMARKRULEQUESTION
BENCHMARKRULEREFERENCE
BENCHMARKRULEREQUIRE
BENCHMARKRULERESULT
BENCHMARKRULERESULTFORBENCHMARKTESTRESULT
BENCHMARKRULERESULTMETADATA
BENCHMARKRULESTATUS
BENCHMARKRULETITLE
BENCHMARKRULEWARNING
BENCHMARKSCORE
BENCHMARKSCOREFORBENCHMARKTESTRESULT
BENCHMARKSTATUS
BENCHMARKSUB
BENCHMARKSUBFORBENCHMARKFIXTEXT
BENCHMARKSUBFORFIXACTION
BENCHMARKSUBGROUP
BENCHMARKTAILORING
BENCHMARKTAILORINGDCSTATUS
BENCHMARKTAILORINGFILE
BENCHMARKTAILORINGMETADATA
BENCHMARKTAILORINGSTATUS
BENCHMARKTESTRESULT
BENCHMARKTESTRESULTASSET
BENCHMARKTESTRESULTASSETSYNTHETICID
BENCHMARKTESTRESULTCREDENTIAL
BENCHMARKTESTRESULTFORBENCHMARKCHECKCONTENTREF
BENCHMARKTESTRESULTMETADATA
BENCHMARKTESTRESULTORGANISATION
BENCHMARKTESTRESULTREMARK
BENCHMARKTESTRESULTSETCOMPLEXVALUE
BENCHMARKTESTRESULTSETVALUE
BENCHMARKTESTRESULTTARGETFACT
BENCHMARKTESTRESULTTITLE
BENCHMARKTITLE
BENCHMARKVALUE
BENCHMARKVALUECHOICE
BENCHMARKVALUECHOICES
BENCHMARKVALUECHOICESFORBENCHMARKVALUE
BENCHMARKVALUECOMPLEXDEFAULT
BENCHMARKVALUECOMPLEXVALUE
BENCHMARKVALUEDCSTATUS
BENCHMARKVALUEDEFAULT
BENCHMARKVALUEDESCRIPTION
BENCHMARKVALUEFORBENCHMARKGROUP
BENCHMARKVALUELOWERBOUND
BENCHMARKVALUEMATCH
BENCHMARKVALUEMATCHFORBENCHMARKVALUE
BENCHMARKVALUEMETADATA
BENCHMARKVALUEQUESTION
BENCHMARKVALUEREFERENCE
BENCHMARKVALUESOURCE
BENCHMARKVALUESTATUS
BENCHMARKVALUETITLE
BENCHMARKVALUEUPPERBOUND
BENCHMARKVALUEVALUE
BENCHMARKVALUEWARNING
BUSINESSIMPACT
BUSINESSIMPACTFORBUSINESSRISK
BUSINESSIMPACTFORREGULATORYRISK
BUSINESSPROCESS
BUSINESSRISK
CAPEC
CAPECREFERENCE
CAPECREFERENCEAUTHOR
CAPECREFERENCEFORCAPEC
CAPECRELATIONSHIP
CATEGORY
CCE
CCEFORASSET
CCEFORCPE
CCEFORTHREATACTORTTP
CCEPARAMETER
CCEPARAMETERFORCCE
CCEREFERENCE
CCEREFERENCEFORCCE
CCERESOURCE
CCERESOURCEAUTHOR
CCERESOURCEFORCCE
CCERESOURCEFORCCEREFERENCE
CCETECHNICALMECHANISM
CCETECHNICALMECHANISMFORCCE
CERTIFICATE
CERTIFICATION
CHARACTERENCODING
CHECKENUMERATION
CHECKLIST
CHECKLISTCATEGORY
CHECKLISTQUESTION
CIAIMPACTFORCAPEC
COASTAGE
COLLECTIONMETHOD
COMMAND
COMMANDS
COMPLIANCE
COMPLIANCECATEGORY
COMPRESSION
CONCATFUNCTION
CONDITION
CONDITIONAPPLICATION
CONFIDENCELEVEL
(Confidence in the information)
CONNECTION
CONNECTIONFORASSET
CONTACT
CONTACTTYPE
CONTENTENUMERATION
CONTROLSTRENGTH
COUNTFUNCTION
COUNTRY
CPE
CPEBLACKLIST
CPEFORAPPLICATION
CPEFORASSET
CPEFORBENCHMARKPLATFORM
CPEFORFIXACTION
CPEFORORGANISATION
CPEFOROS
CPEFORPLATFORM
CPEPORT
CPEWHITELIST
CRE
CREFORCPE
CREPARAMETER
CREPARAMETERS
CREPERSON
CREREFERENCE
CWE
CWEFORCAPEC
CWEFOROWASPTOP10
CWETOP25
CWEWASC
CYBEROBJECT
CYBEROBJECTCYBEROBJECTPROPERTIES
CYBEROBJECTDOMAINSPECIFICPROPERTY
CYBEROBJECTEFFECT
CYBEROBJECTFORCYBEROBJECT
CYBEROBJECTFORCYBEROBSERVABLE
CYBEROBJECTPOOL
CYBEROBJECTPOOLCYBEROBJECT
CYBEROBJECTPROPERTIES
CYBEROBJECTPROPERTIESFORCYBEROBJECT
CYBEROBJECTPROPERTY
CYBEROBJECTPROPERTYFORCYBEROBJECTPROPERTIES
CYBEROBJECTPROPERTYFORCYBEROBJECTPROPERTY
CYBEROBJECTPROPERTYGROUP
CYBEROBJECTPROPERTYPATTERNFIELDGROUP
CYBEROBJECTTYPE
CYBEROBSERVABLE
CYBEROBSERVABLEFORCYBEROBSERVABLES
CYBEROBSERVABLEFORINCIDENT
CYBEROBSERVABLEFORINDICATOR
CYBEROBSERVABLEFORTHREATINFRASTUCTURE
CYBEROBSERVABLEKEYWORD
CYBEROBSERVABLES
CYBEROBSERVABLETESTMECHANISM
DATAFORMAT
DATASEGMENT
DATASIZEUNIT
DATATYPE
DATETIMEFORMAT
DCSTATUS
DEBUGGINGACTIONNAME
DEFENSETOOLTYPE
DETECTABILITY
DEVICE
DEVICEBLACKLIST
DEVICECOMPONENT
DEVICECOMPONENTFORDEVICE
DEVICECOMPONENTFORDEVICECOMPONENT
DEVICEDRIVERACTIONNAME
DEVICEWHITELIST
DIRECTORYACTIONNAME
DISCOVERYMETHOD
DISKACTIONNAME
DNSACTIONNAME
DPE
EFFECTIVENESS
EFFECTTYPE
EMAIL
EMAILADDRESS
EMAILFORORGANISATION
EMAILFORPERSON
ENCODING
ENCRYPTION
ENDFUNCTION
ENDPOINT
ENVIRONMENT
ESCAPEREGEXFUNCTION
EVENT
EVENTCOLLECTIONMETHOD
EVENTCOMMENT
EVENTCOMMENTFOREVENT
EVENTENDPOINT
EVENTFORASSET
EVENTFOREVENT
EVENTFORINCIDENT
EVENTPROPERTY
EVENTPROPERTYADDRESS
EVENTPROPERTYFOREVENT
EVENTSIGNATURE
EVENTTYPE
EXISTENCEENUMERATION
EXPLOIT
EXPLOITABILITY
EXPLOITAUTHOR
EXPLOITFORCPE
EXPLOITFORREFERENCE
EXPLOITFORTHREATACTORTTP
EXPLOITFORVULNERABILITY
EXPLOITLIKELIHOOD
EXPLOITLIKELIHOODFORATTACKPATTERN
EXPLOITOSINSTRUCTIONMEMORYADDRESS
EXPLOITPARAMETER
EXPLOITPARAMETERFOREXPLOIT
EXPOSURELEVEL
FILEACTIONNAME
FILTERACTION
FINDING
FIXACTION
FIXACTIONCOST
FIXACTIONFORBENCHMARKRULERESULT
FIXACTIONFORFIXACTION
FIXACTIONFORINCIDENT
FIXACTIONFORVULNERABILITY
FIXSYSTEM
FLAG
FRAMEWORK
FRAMEWORKFORTECHNICALCONTEXT
FREQUENCY
FTPACTIONNAME
FUNCTION
FUNCTIONARGUMENT
GEOLOCATION
GROUPINGRELATIONSHIP
GUIACTIONNAME
GUIDELINE
GUIDELINEFORATTACKPATTERN
HASHNAME
HASHVALUE
HOOKINGACTIONNAME
HTTPACTIONNAME
IDENTIFICATIONSYSTEM
IMPACT
IMPORTANCETYPE
INCIDENT
INCIDENTCATEGORY
INCIDENTCOMPROMISE
INCIDENTDISCOVERYMETHOD
INCIDENTEFFECT
INCIDENTFORASSET
INCIDENTFORINCIDENT
INCIDENTFORPERSON
INCIDENTFORTHREATCAMPAIGN
INCIDENTID
INCIDENTIMPACT
INCIDENTIMPACTAVAILABILITYLOSSDURATION
INCIDENTIMPACTAVAILABILITYVARIETY
INCIDENTIMPACTCONFIDENTIALITYSTATE
INCIDENTIMPACTCONFIDENTIALITYVARIETY
INCIDENTIMPACTINTEGRITYVARIETY
INCIDENTIMPACTLOSSPROPERTY
INCIDENTIMPACTLOSSRATING
INCIDENTIMPACTLOSSVARIETY
INCIDENTIMPACTRATING
INCIDENTINQUIRY
INCIDENTINQUIRYINTENT
INCIDENTIOC
INCIDENTIOCFORTHREATCAMPAIGN
INCIDENTIOCTYPE
INCIDENTIOCTYPEFORINDICATOR
INCIDENTREGISTRYHANDLE
INCIDENTSTATUS
INCIDENTTIMELINE
INCIDENTTIMELINEUNIT
INDICATOR
INDICATORFORINDICATOR
INDICATORID
INDICATORIDFORINCIDENTIOC
INDICATORIDFORINDICATOR
INFORMATIONSOURCETYPE
INFORMATIONTYPE
INFORMATIONTYPEFORTHREATACTORTTP
INFRASTRUCTURE
(To be defined)
INJECTIONVECTOR
INJECTIONVECTORFORATTACKPATTERN
INSTANCE
INSTRUCTION
INTERFACE
INTERFACEFORSYSTEMINFO
IPCACTIONNAME
IRCACTIONNAME
ISOCURRENCY
KEYWORD
KILLCHAIN
KILLCHAINFORTHREATACTORTTP
KILLCHAINPHASE
KILLCHAINPHASEFORKILLCHAIN
KILLCHAINPHASEFORTHREATACTORTTP
LANGUAGE
LANGUAGEFORAPPLICATION
LANGUAGEFORTECHNICALCONTEXT
LANGUAGEFUNCTION
LIBRARYACTIONNAME
LOCALE
LOCATIONPOINT
LOCATIONPOINTFORASSET
LOCATIONPOINTFORORGANISATION
LOCATIONPOINTFORPERSON
LOCATIONREGION
LOCATIONREGIONFORASSET
LOSSFACTOR
LOSSFORM
LOSSPROPERTY
LOSSPROPERTYFORINCIDENT
MACHINE
(ASSET)
MALWAREENTITY
MALWAREINSTANCE
MALWARENAME
MALWARENAMEFORMALWAREINSTANCE
MALWARESUBJECTRELATIONSHIP
MALWARETYPE
MALWARETYPEFORMALWAREINSTANCE
MATURITYRATING
MEASURESOURCE
MEASURESOURCECONTRIBUTOR
MEASURESOURCEINFORMATIONSOURCETYPE
MEASURESOURCEPLATFORM
MEASURESOURCESYSTEM
MEASURESOURCETOOL
MEASURESOURCETOOLTYPE
MEMORYADDRESS
MESSAGELEVEL
METADATA
METHODOLOGY
MIME
MISSION
MITIGATION
MITIGATIONFORATTACKPATTERN
NAICS
NETWORKACTIONNAME
NETWORKSHAREACTIONNAME
OBFUSCATIONTECHNIQUE
OBJECTRELATIONSHIP
OBJECTSTATE
OBSERVATIONMETHOD
OPCODE
OPCODEFORCPE
OPERATION
(PROJECT)
OPERATIONALATTRIBUTE
OPERATIONENUMERATION
OPERATIONENUMERATIONFORSIMPLEDATATYPE
OPERATIONMISSION
OPERATORENUMERATION
ORGANISATION
ORGANISATIONFORTHREATACTORTTP
ORGANIZATIONALUNIT
ORGANIZATIONALUNITFORORGANISATION
OS
(Comes from first implementation: CPE+LOCALE)
OSFAMILY
OSFAMILYFOROS
OSILAYER
OSILAYERFORATTACKSURFACE
OSINSTRUCTIONMEMORYADDRESS
OSPATCHLEVEL
OSPATCHLEVELPATCH
OVALAFFECTED
OVALAFFECTEDFOROVALMETADATA
OVALAFFECTEDPLATFORM
OVALAFFECTEDPRODUCT
OVALBEHAVIOR
OVALBEHAVIORFOROVALOBJECT
OVALCLASSDIRECTIVES
OVALCLASSDIRECTIVESFOROVALDIRECTIVES
OVALCLASSDIRECTIVESFOROVALRESULTS
OVALCLASSENUMERATION
OVALCOMPONENTGROUP
OVALCOMPONENTGROUPFORARITHMETICFUNCTION
OVALCOMPONENTGROUPFORCONCATFUNCTION
OVALCOMPONENTGROUPFORCOUNTFUNCTION
OVALCOMPONENTGROUPFOROVALLOCALVARIABLE
OVALCOMPONENTGROUPFORTIMEDIFFERENCEFUNCTION
OVALCOMPONENTGROUPFORUNIQUEFUNCTION
OVALCONSTANTVARIABLE
OVALCONSTANTVARIABLEVALUE
OVALCRITERIA
OVALCRITERIAFOROVALCRITERIA
OVALCRITERIATYPE
OVALCRITERIATYPEFOROVALDEFINITIONTYPE
OVALCRITERION
OVALCRITERIONFOROVALCRITERIA
OVALCRITERIONTYPE
OVALCRITERIONTYPEFOROVALCRITERIATYPE
OVALDEFAULTDIRECTIVES
OVALDEFINITION
OVALDEFINITIONORGANISATION
OVALDEFINITIONS
OVALDEFINITIONSTATUS
OVALDEFINITIONTYPE
OVALDEFINITIONTYPEFOROVALSYSTEMTYPE
OVALDIRECTIVE
OVALDIRECTIVES
OVALDIRECTIVESTYPE
OVALENTITYATTRIBUTEGROUP
OVALENTITYCOMPLEXBASE
OVALENTITYSIMPLEBASE
OVALEXTENDDEFINITION
OVALEXTENDDEFINITIONFOROVALCRITERIA
OVALEXTENDDEFINITIONTYPE
OVALEXTENSIONPOINT
OVALEXTENSIONPOINTFOROVALGENERATORTYPE
OVALEXTENSIONPOINTFOROVALMETADATA
OVALEXTENSIONPOINTFORSYSTEMINFO
OVALEXTERNALVARIABLE
OVALFILTER
OVALFILTERFOROVALSET
OVALFUNCTIONGROUP
OVALFUNCTIONGROUPFOROVALCOMPONENTGROUP
OVALGENERATORTYPE
OVALITEM
OVALITEMATTRIBUTEGROUP
OVALITEMCOMPLEXBASE
OVALITEMFOROVALSYSTEMOBJECT
OVALITEMSIMPLEBASE
OVALLITERALCOMPONENT
OVALLITERALCOMPONENTFOROVALCOMPONENTGROUP
OVALLOCALVARIABLE
OVALMESSAGETYPE
OVALMESSAGETYPEFOROVALDEFINITIONTYPE
OVALMESSAGETYPEFOROVALITEM
OVALMESSAGETYPEFOROVALSYSTEMOBJECT
OVALMESSAGETYPEFOROVALTESTEDITEM
OVALMESSAGETYPEFOROVALTESTTYPE
OVALMETADATA
OVALMETADATACCE
OVALMETADATACPE
OVALMETADATAREFERENCE
OVALMETADATAVULNERABILITY
OVALOBJECT
OVALOBJECTCOMPONENT
OVALOBJECTCOMPONENTFOROVALCOMPONENTGROUP
OVALOBJECTFIELD
OVALOBJECTFIELDFOROVALOBJECTRECORD
OVALOBJECTFOROVALSET
OVALOBJECTFOROVALTEST
OVALOBJECTRECORD
OVALOBJECTRECORDFOROVALOBJECT
OVALRESULTS
OVALRESULTSTYPE
OVALSET
OVALSETFOROVALSET
OVALSTATE
OVALSTATECOMPLEXBASE
OVALSTATEFIELD
OVALSTATEFIELDFOROVALSTATERECORD
OVALSTATEFOROVALTEST
OVALSTATERECORD
OVALSTATERECORDFOROVALSTATE
OVALSTATESIMPLEBASE
OVALSYSTEMCHARACTERISTICS
OVALSYSTEMOBJECT
OVALSYSTEMTYPE
OVALSYSTEMTYPEFOROVALRESULTSTYPE
OVALTEST
OVALTESTEDITEM
OVALTESTEDITEMFOROVALTESTTYPE
OVALTESTEDVARIABLE
OVALTESTEDVARIABLEFOROVALTESTTYPE
OVALTESTFOROVALTESTS
OVALTESTS
OVALTESTTYPE
OVALTESTTYPEFOROVALSYSTEMTYPE
OVALVARIABLE
OVALVARIABLECOMPONENT
OVALVARIABLECOMPONENTFOROVALCOMPONENTGROUP
OVALVARIABLEFOROVALVARIABLES
OVALVARIABLES
OVALVARIABLEVALUE
OVALVARIABLEVALUEFOROVALSYSTEMOBJECT
OWASPTOP10
OWASPTOP10ATTACKVECTOR
OWASPTOP10DEFENSETOOLTYPE
OWASPTOP10DETECTABILITY
OWASPTOP10EXPLOITABILITY
OWASPTOP10IMPACT
OWASPTOP10PREVALENCE
OWASPTOP10REFERENCE
OWASPTOP10TOOLINFORMATION
PACKAGING
PACKAGINGCOMPRESSION
PACKAGINGENCODING
PACKAGINGENCRYPTION
PATCH
PATCHBUNDLE
PATCHFORCPE
PATCHFORDEVICE
PATCHFORDEVICECOMPONENT
PATCHFORPATCHBUNDLE
PATCHFORPATCHLEVEL
PATCHLEVEL
PATCHREFERENCE
PATTERNFIELDGROUP
PATTERNTYPE
PERSON
PERSONDEVICE
PERSONFORAPPLICATION
PERSONFORASSET
PERSONFORINCIDENT
PERSONFORMISSION
PERSONFORORGANISATION
PERSONFORPERSONGROUP
PERSONFORPROJECT
PERSONFORTHREATACTORTTP
PERSONGROUP
PHYSICALLOCATION
PKI
PLATFORM
PLATFORMFORCCE
PLATFORMFORTECHNICALCONTEXT
POLICY
PORT
PORTFOREXPLOIT
PORTFORVULNERABILITY
PORTPROTOCOL
POSSIBLERESTRICTION
POSSIBLERESTRICTIONFOROVALEXTERNALVARIABLE
POSSIBLEVALUE
POSSIBLEVALUEFOROVALEXTERNALVARIABLE
PREVALENCE
PRIORITYLEVEL
PROBINGTECHNIQUE
PROBINGTECHNIQUEFORATTACKPATTERN
PROCEDURE
PROCESS
PROCESSACTIONNAME
PROCESSMEMORYACTIONNAME
PROCESSORTYPE
PROCESSORTYPEREGISTER
PROCESSTHREADACTIONNAME
PRODUCT
PROJECT
PROJECTFORAPPLICATION
PROJECTFORPROJECT
PROJECTMETHODOLOGY
PROTOCOL
PROTOCOLFORPROTOCOL
RATIONALE
RATIONALEFORBENCHMARKGROUP
RATIONALEFORBENCHMARKRULE
REFERENCE
REGEXCAPTUREFUNCTION
REGISTER
REGISTRYACTIONNAME
REGULATORYRISK
RELATIONSHIPTYPE
REPOSITORY
REPOSITORYFORVOCABULARY
REPORT
REPORTFORREPORTS
REPORTREQUEST
REPORTREQUESTFORREPORTREQUESTS
REPORTREQUESTS
REPORTS
RESTRICTION
RESTRICTIONFORPOSSIBLERESTRICTION
RESULTENUMERATION
RISKRATING
ROPCHAIN
ROPCHAININSTRUCTION
ROPCHAINREFERENCE
ROPGADGET
ROPGADGETFORROPCHAIN
ROPGADGETINSTRUCTION
SCENARIO
SCENARIOFOROWASPTOP10
SCORINGFORMULA
SCORINGSYSTEM
SCORINGSYSTEMFORMULAS
SCORINGSYSTEMREFERENCE
SCRIPT
SECURITYATTRIBUTE
SECURITYATTRIBUTECATEGORY
SECURITYATTRIBUTESTATE
SECURITYATTRIBUTEVARIETY
SECURITYCHANGE
SECURITYCONTROL
SECURITYCONTROLFAMILY
SECURITYCONTROLMAPPING
SECURITYCONTROLSTRENGTH
SECURITYCONTROLTOOL
SECURITYMARKING
SECURITYMETRIC
SECURITYPRINCIPLE
SECURITYPRINCIPLEFORATTACKPATTERN
SECURITYPROGRAM
SECURITYPROGRAMTYPE
SECURITYREQUIREMENT
SECURITYREQUIREMENTFORATTACKPATTERN
SERVICEACTIONNAME
SERVICECATEGORY
SETOPERATOR
SEVERITYLEVEL
SIDTYPE
SIGNATURE
SIGNATURECPE
SIGNATUREEXPLOIT
SIGNATUREMALWAREINSTANCE
SIGNATUREPORT
SIGNATUREPROTOCOL
SIGNATUREREFERENCE
SIGNATURETYPE
SIGNATURETYPEREFERENCE
SIMPLEDATATYPE
SOCKETACTIONNAME
SOURCECLASS
SOURCETYPE
SPLITFUNCTION
STANDARD
STANDARDREFERENCE
STANDARDVOCABULARY
STATUS
SUBSTRINGFUNCTION
SYNCHRONIZATIONACTIONNAME
SYSTEM
SYSTEMACTIONNAME
SYSTEMINFO
SYSTEMINFOFOROVALSYSTEMCHARACTERISTICS
SYSTEMTYPE
SYSTEMTYPEFORASSET
SYSTEMTYPEFORTHREATACTORTTP
TAG
TASK
TASKATTACHMENT
TASKFORPROJECT
TASKPERSON
TECHNICALCONTEXT
TELEPHONE
TELEPHONEFORORGANISATION
TELEPHONEFORPERSON
TESTMECHANISMEFFICACY
TESTMECHANISMEFFICACYFORCYBEROBSERVABLETESTMECHANISM
TESTMECHANISMID
THREATACTION
THREATACTIONCATEGORY
THREATACTIONFORINCIDENT
THREATACTIONLOCATION
THREATACTIONTARGET
THREATACTIONVARIETY
THREATACTIONVARIETYFORTHREATACTORTTP
THREATACTIONVECTOR
THREATACTOR
THREATACTORFORINCIDENT
THREATACTORFORTHREATCAMPAIGN
THREATACTORINFRASTRUCTURE
THREATACTORINFRASTRUCTUREFORTHREATACTOR
THREATACTORINFRASTRUCTUREFORTHREATACTORTTP
THREATACTORPAOS
THREATACTORROLE
THREATACTORSKILL
THREATACTORSKILLFORATTACKPATTERN
THREATACTORTTP
THREATACTORTTPFORINCIDENT
THREATACTORTTPFORINDICATOR
THREATACTORTTPFORTHREATACTORTTP
THREATACTORVARIETY
THREATAGENT
THREATAGENTFOROWASPTOP10
THREATCAMPAIGN
THREATCAMPAIGNFORTHREATCAMPAIGN
THREATCAMPAIGNNAME
THREATCAMPAIGNNAMEFORTHREATCAMPAIGN
THREATCAMPAIGNSTATUS
THREATCAMPAIGNTYPE
THREATINTENDEDEFFECT
THREATINTENDEDEFFECTFORINCIDENT
THREATINTENDEDEFFECTFORTHREATACTORTTP
THREATINTENDEDEFFECTFORTHREATCAMPAIGN
THREATMOTIVE
THREATMOTIVEFORTHREATACTOR
TICKET
TIMEDIFFERENCEFUNCTION
TIMEUNIT
TOOLINFORMATION
TOOLINFORMATIONMETADATA
TOOLINFORMATIONREFERENCE
TOOLREFERENCETYPE
TOOLTYPE
TOOLTYPEFORTOOLINFORMATION
TRAINING
TRAININGFORPERSON
TREND
TRUSTLEVEL
UNIQUEFUNCTION
USECASE
USECASEFORBUSINESSRISK
USECASEFORREGULATORYRISK
USERACTIONNAME
VALUE
VOCABULARY
VOCABULARYREFERENCE
VULNERABILITY
VULNERABILITYFORATTACKEXAMPLE
VULNERABILITYFORATTACKPATTERN
VULNERABILITYFORCPE
VULNERABILITYFORCWE
VULNERABILITYFORREFERENCE
VULNERABILITYFORSTANDARD
VULNERABILITYFORTHREATACTION
VULNERABILITYFORTHREATACTORTTP
VULNERABILITYMAPPING
VULNERABILITYPATCH
VULNERABILITYSCORE
WAIVER
WARNING
WARNINGCATEGORY
WASC
WASCREFERENCE
All trademarks and registered trademarks are the property of their respective owners.
|
|



